Layered Encryption Breakdown: Decoding Nested Base64 and ROT13 to Reveal Hidden Flag
What Happens
This cryptography challenge highlights systematic problem-solving by breaking through multiple layers of encoding. The payload was first decoded from Base64, then decoded again, only to reveal text disguised using ROT13 shifting. By correctly recognizing each cipher and applying the appropriate decoding method step-by-step, the true flag was successfully uncovered — a workflow that reflects real-world cybersecurity analysis.
What I Did
After downloading the file I got this encoded base64 String
YidkM0JxZGtwQlRYdHFhR3g2YUhsZmF6TnFlVGwzWVROclgyeG9OakJzTURCcGZRPT0nCg==Put it into cyberchef and decode it from base64 then I got this result
b'd3BqdkpBTXtqaGx6aHlfazNqeTl3YTNrX2xoNjBsMDBpfQ=='the result contains base64 encoded String inside ‘ symbol and some weird “b” character at start, so I tried remove the “b” and the ‘ symbol then decode it again and this is the result
wpjvJAM{jhlzhy_k3jy9wa3k_lh60l00i}the String have similar structure with the picoCTF Flag answer, but it’s still not the right string, looking back at the question tag there is “caesar” tag which make me think this is encoded with caesar where each character is just shifted by certain amount,
so I put it back to cyberchef and choose ROT13 as recipe because it might be just a simple shift then just playing with the amount number until i got the result
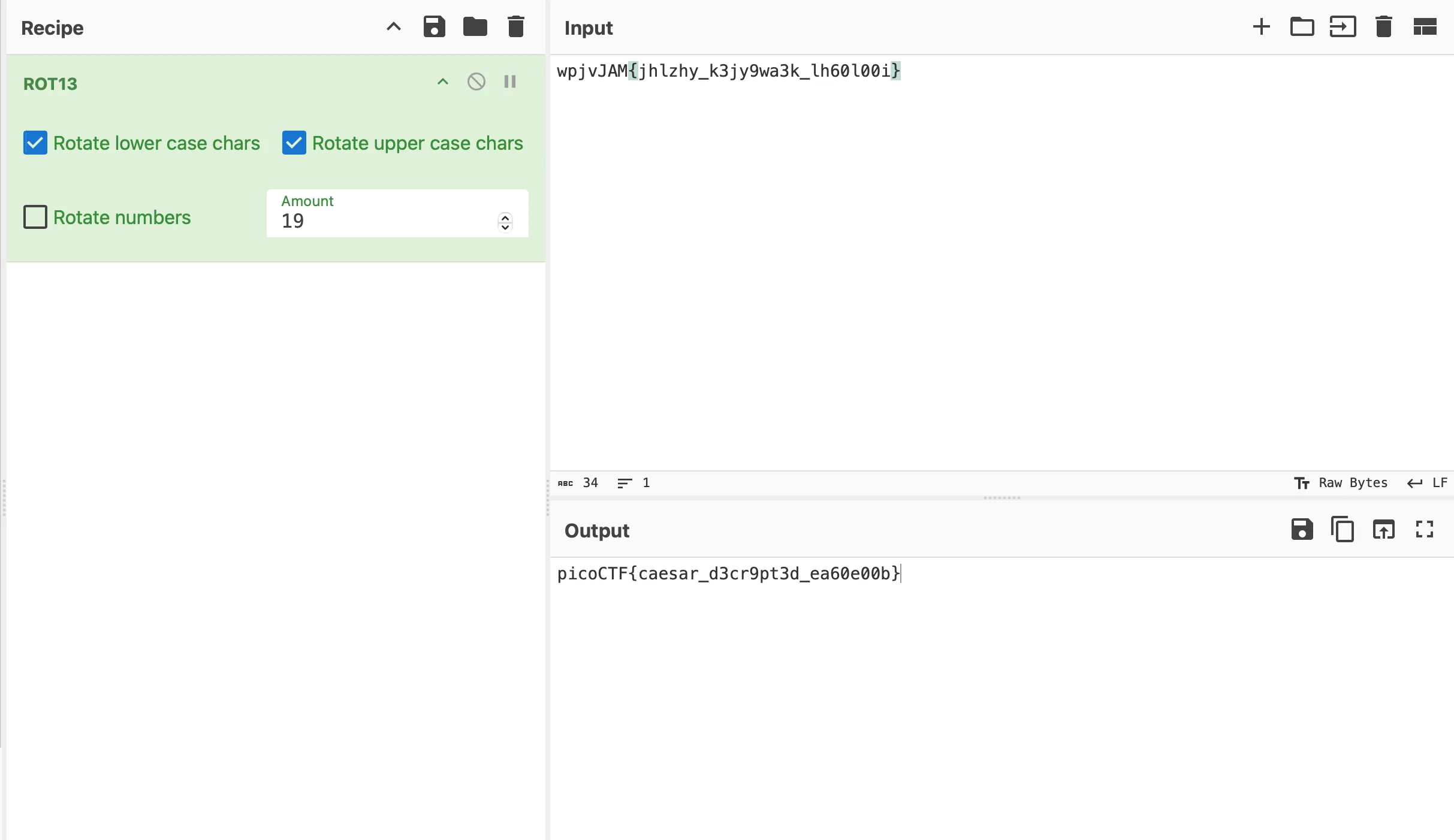
and the flag is
picoCTF{caesar_d3cr9pt3d_ea60e00b}