Static Analysis of React Native APK: Extracting Hard-Coded API Tokens Through Bundle Inspection
What Happens
This challenge showcases a practical mobile security workflow by performing static analysis on a React Native APK to uncover exposed API credentials. After reversing the application with JADX and manually inspecting the bundle, the hard-coded token was identified and used to access the API endpoint — successfully retrieving the flag. The steps reflect real-world techniques used in mobile application penetration testing and source code audits.
What I Did
import APK to JADX then open MainActivity
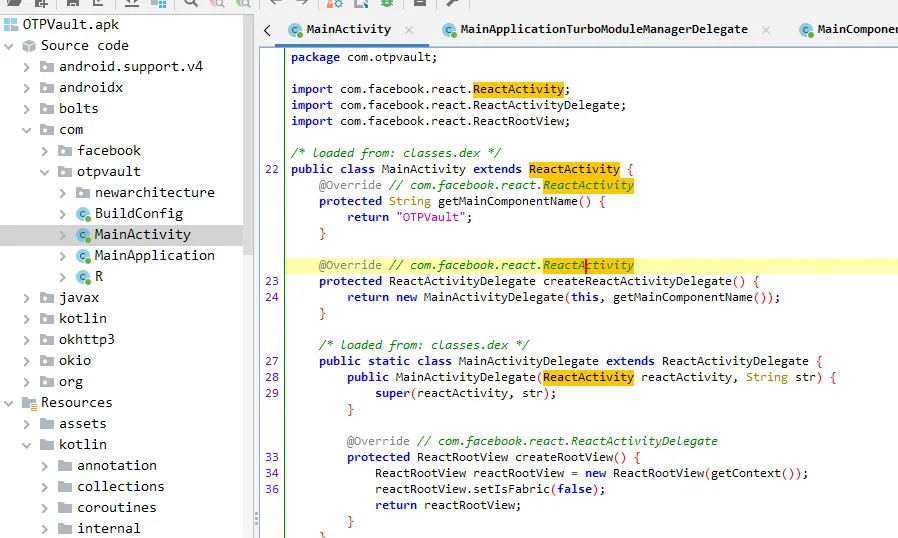
since the app uses React Native (by checking the comment and import) we need to reverse the app differently.
because react-native is a JavaScript framework I tried to unzip the OTPVault.apk
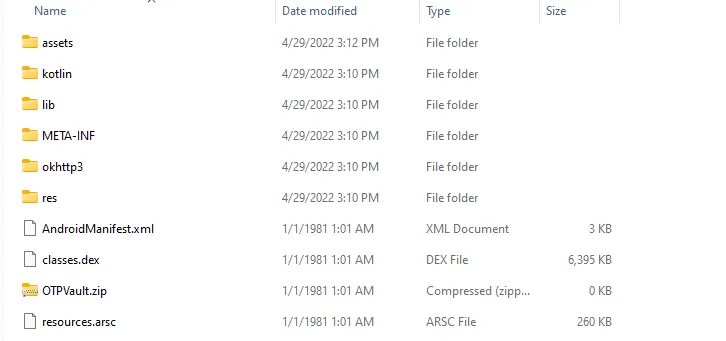
Go to assets then open index.android.bundle using notepad / VS Code
copy all the code then beautify it at Online JavaScript beautifier or using built-in VS Code to make it more readable
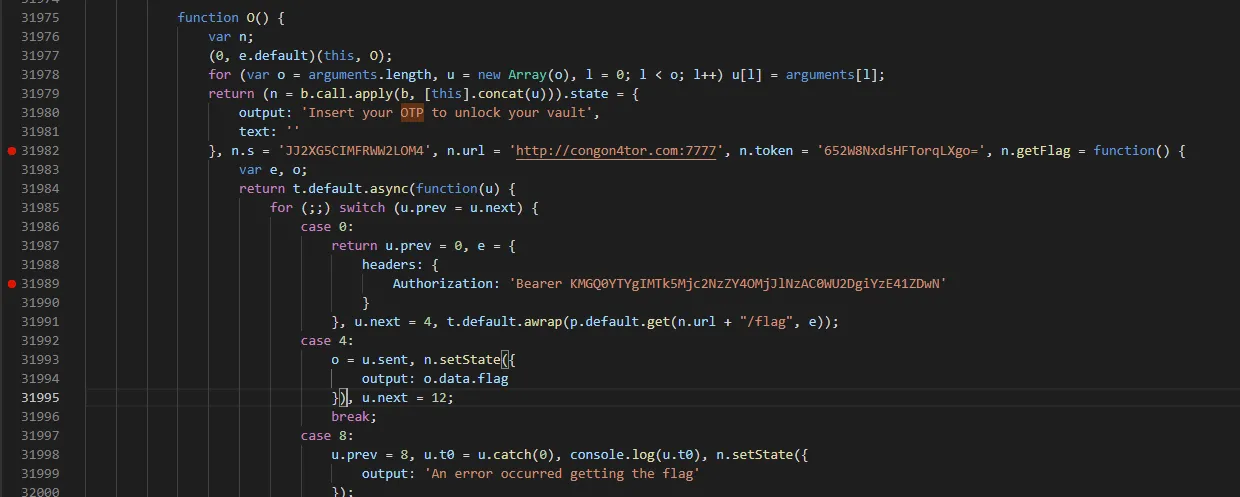
since I got the endpoint to get OTP and the token, I use Postman to call it with this configuration
Method: GET
URL: http://congon4tor.com:7777/flag
Auth: Bearer Token KMGQ0YTYgIMTk5Mjc2NzZY4OMjJlNzAC0WU2DgiYzE41ZDwN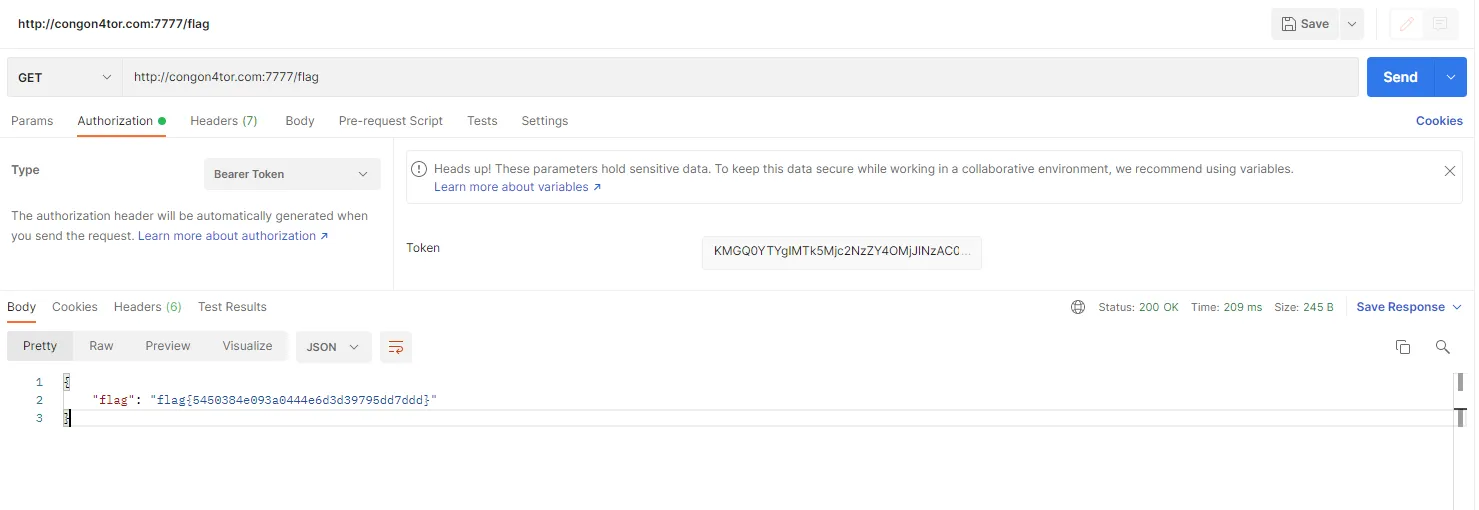
then….. the result status is 200 and the flag shown
flag{5450384e093a0444e6d3d39795dd7ddd}